WHITE PAPER: CMMC Compliance–A New and Unique Approach
-By Raymond Hutchins and Mitch Tanenbaum
Abstract: Cybersecurity and DoD contract pros explain why IT enclaves may be the FASTEST, possibly ONLY and least expensive way to comply with CMMC certification and 800-171 CUI requirements. They also explain how to get reimbursed for expenses associated with compliance with the still evolving CMMC certification requirements and building a secure enclave.
Table of Contents
- 1. The Basics
- 2. Is CMMC compliance/certification even remotely possible?
- 3. What is a secure “enclave”?
- 4. What are the purposes of secure enclaves?
- 5. Who says an enclave can be used to protect CUI and other sensitive information?
- 6. What is your first decision regarding a possible enclave strategy?
- 7. What types of enclave strategies are there?
- 8. What are the FIRST TASKS associated with building a secure CUI enclave?
- 9. Which enclave strategy is best for you?
- 10. Three CUI Enclave Use Cases
- 11. How to get paid for complying with 800-171
- 12. Cost and Other Issues Related to the Necessary Use of the Microsoft Government Cloud for enclaves
- 13. Calculating Enclave Costs
- 14. What are MSP/MSSP requirements associated with an enclave environment?
- 15. Why choose us as your CMMC/800-171 partner? --Our CMMC Level 2 Enclave Certification Program
1. The Basics:
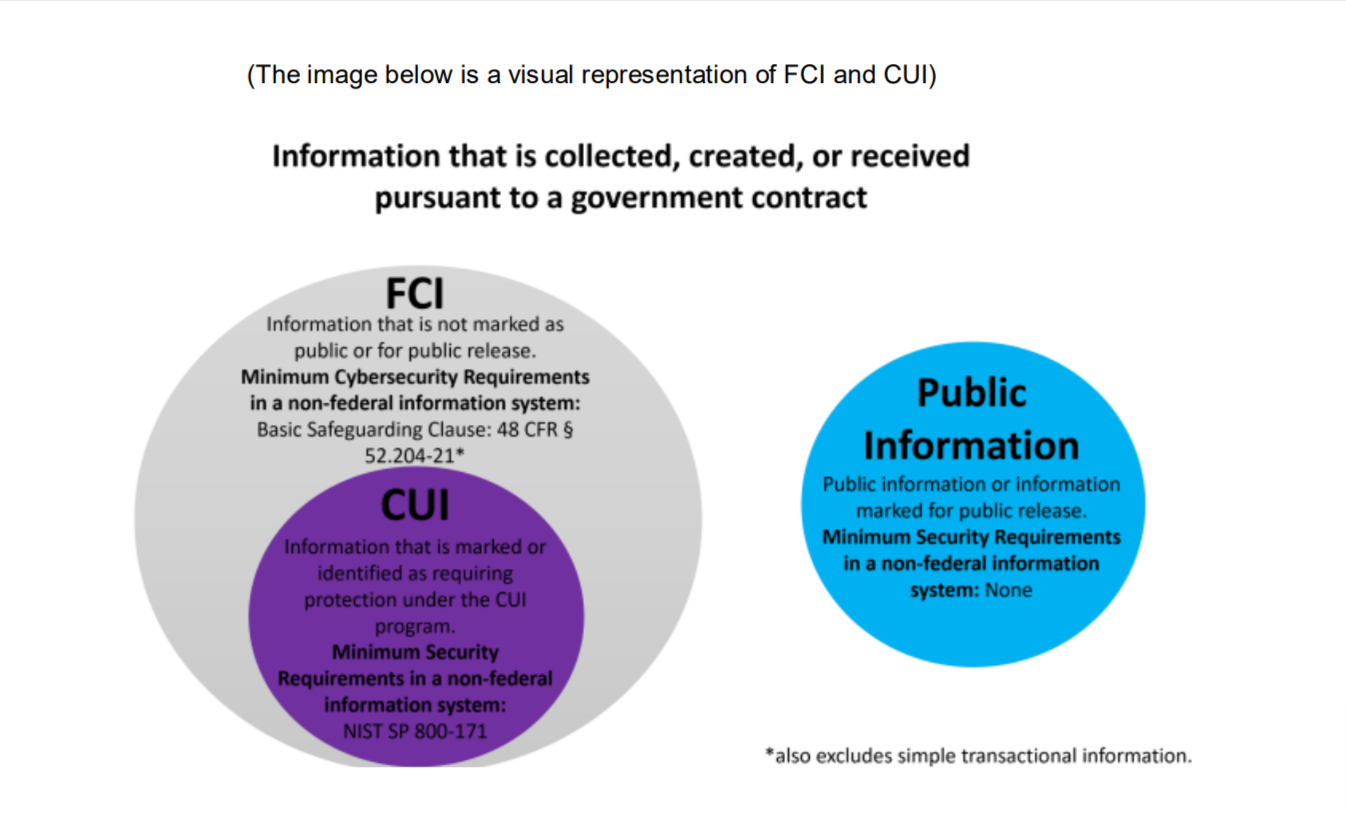
What is CUI–does anyone really know?
Who has to comply with CMMC?
When Is compliance required?
...and more frequently asked questions are answered here: 800-171 /CMMC 2.0 Overview
2. Is CMMC compliance/certification even remotely possible?
For the vast majority of companies that will ultimately have to be certified, the answer (until now) has been no. It’s just too hard.
This is evidenced by the vast, ongoing fraud tolerated by DoD towards the Defense Industrial Base (DIB). The DIB continues to legally attest that it is complying with the contract requirements while the DoD turns a blind eye…not because no one cares…because it is too hard for the average enterprise to accomplish. Please continue reading to discover why that is. Recently, the Department of Justice has started prosecuting liars.
And the DoD has yet to roll out the compliance plan, mechanisms, systems, and support required for wide-spread and fast improvement. And most importantly, the DoD has not put forth a plan for funding the security upgrade.
While DoD engages in its internal processes, businesses can harness existing cloud technologies and Microsoft applications to quickly identify, segment, and protect CUI and associated systems into parallel IT enclave systems designed to protect the DIB data assets.
CMMC certification is required of any company in the DOD supply chain, including contractors whether their business works exclusively with the Department of Defense or not and any and all subcontractors that have access to CUI. According to the DOD, the CMMC requirements may affect over 300,000 organizations.
One of DoD’s objectives with CMMC is to significantly reduce the number of companies that have access to CUI. The requirements for protecting FCI vs. CUI are trivial and those companies can self-certify. If DoD can reduce the number of companies who have access to CUI by, say, half, that greatly reduces the attack surface. In addition, DoD is talking about the possibility that a few of those remaining contractors who have access to CUI may also be able to self certify, although how that would work has not been defined.
If you take that 300,000 number and say that 100,000 only have access to FCI, and then if you say that of the remaining 200,000, 50,000 of those do not need access to CUI to get their job done, and then if you say that of the remaining 150,000, 30,000 of those can self-certify, then you have reduced the problem from 300,000 to 120,000, which, while not a simple problem to solve, is simpler.
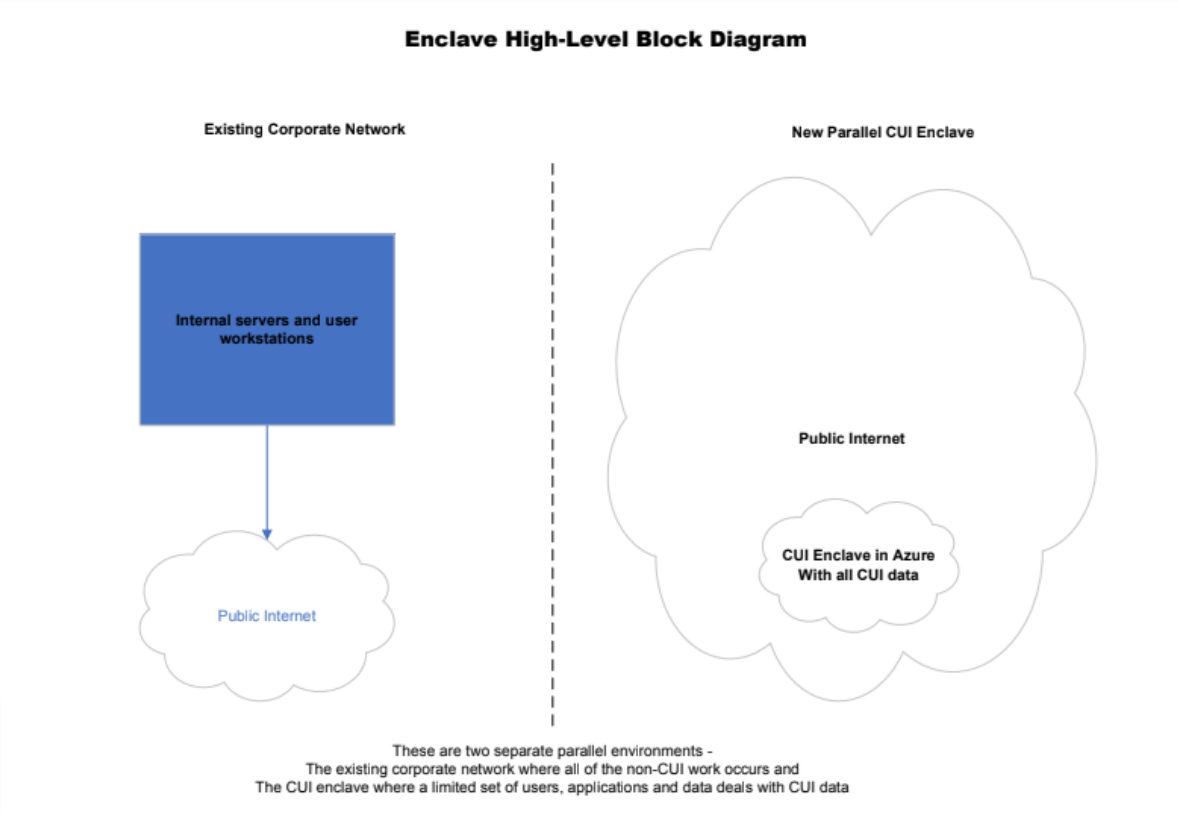
3. What is a secure “enclave”?
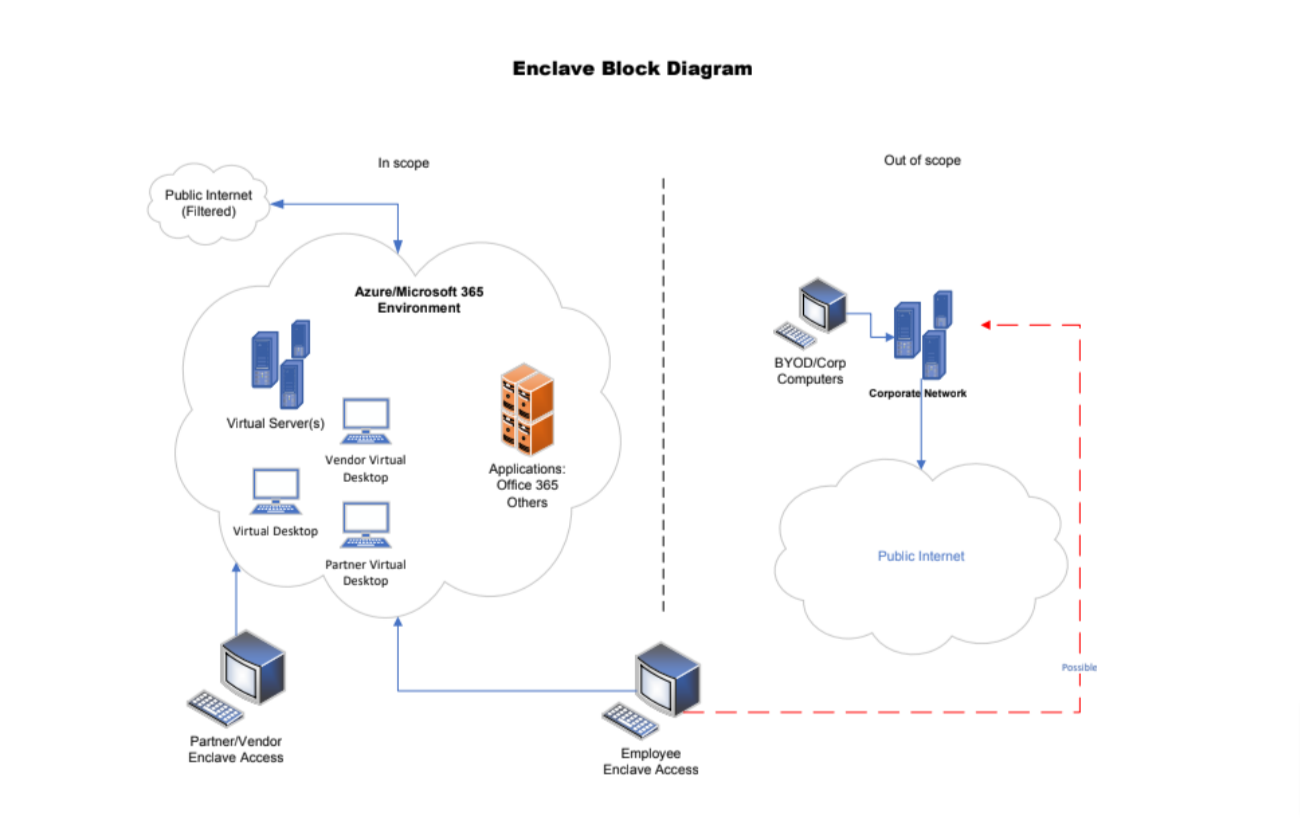
A secure enclave is a portion (or segment) of an IT infrastructure that's separated from the rest of the infrastructure, and which is governed by a different set of security policies. Secure enclaves are typically run in parallel with other, preexisting IT infrastructures. Please see enclave diagram here:
4. What are the purposes of secure enclaves?
- Enforce least-privileged access to critical resources as part of a defense-in-depth security strategy.
- Enclaves isolate the more sensitive information (CUI) from the rest of the information, making it easier to protect.
- Enclaves have much tighter security practices. Since only a limited number of people will have access to an enclave and only when they are accessing CUI, you have reduced the “pain” that the majority of the people have to deal with.
- Because an enclave is smaller and a limited number of people accessing it, a limited amount of software in it and a limited amount of data, protecting an enclave is easier than protecting the entire IT infrastructure.
- Companies can also allow subcontractors to access the contractor’s enclave, making it simpler for subs to participate in a project.
5. Who says an enclave can be used to protect CUI and other sensitive information?
What is the authority behind the requirement to protect CUI? Here is what the DoD and the National Institute of Standards (NIST) says about the subject in Section 1.1 of NIST 800-171 :
- The requirements apply to components of nonfederal systems that process, store, or transmit CUI, or that provide security protection for such components. If non-federal organizations designate specific system components for the processing, storage, or transmission of CUI, those organizations may limit the scope of the security requirements by isolating the designated system components in a separate CUI security domain.
- Isolation can be achieved by applying architectural and design concepts (e.g., implementing subnetworks with firewalls or other boundary protection devices and using information flow control mechanisms).
- Security domains may employ physical separation, logical separation, or a combination of both.
- This approach can provide adequate security for the CUI and avoid increasing the organization’s security posture to a level beyond that which it requires for protecting its missions, operations, and assets.
6. What is your first decision regarding a possible enclave strategy?
With respect to protecting CUI, you only have two options:
- Upgrade your entire IT infrastructure to meet the protection requirements for CUI.
- Create a new, separate, parallel enclave IT infrastructure to house the CUI information and associated business processes.
7. What types of enclave strategies are there?
Greenfield Enclave Strategy
- Only for a new project (contract or part of contract)
- Only if required for a contract. Look for specific CUI control requirements in the language of the contract vehicle.
- Include the minimum number of people you can
- Include the minimum number of applications you can
- Include the least amount of data you can
- Beware of and control scope creep
- What is the support strategy–internal/external. If external and the external provider can get access to your data, their security is part of your security. Look at the security of the provider and possible certification requirements (eventually) of the provider. (See MSP)
- If there are cloud applications, including cloud security applications, that complicates things and adds new requirements.
Brownfield Enclave Strategy
- Typically best for any existing contracts
- Everything in the Greenfield Strategy, plus
- Data inventory
- Data cleanup
- Migration planning (what to migrate–more than data-domain users?)
- Migration execution
8. What are the FIRST TASKS associated with building a secure CUI enclave?
- Identify what information you have or will receive that will be categorized as CUI
- Identify which people (internal or external) who will need access to this information
- Identify what business processes that will need to interact with this data
- Determine which enclave strategy is best for your situation and organization
9. Which enclave strategy is best for you?
Two scenarios:
- You already have one or more Federal contracts and now you are considering another one……..or
- This is a new Federal contract opportunity that contains CUI
Question: Can your company currently meet the project’s or contract’s CUI requirements with your existing IT infrastructure and processes?
If your answer is YES. In this case, you likely have already had an 800-171 risk assessment and you have achieved a score of approx. 110. In this case, an enclave is not necessary.
If your answer is NO: Then it will be necessary to upgrade your existing IT infrastructure to meet CUI requirements, not bid on the contract or implement some sort of enclave.
Also, the time has come to answer the following questions:
- Have you identified all Federal contracts the company is engaged in that contain CUI?
- Can you still meet other business requirements while managing this project/contract inside a secure enclave? (see enclave definition above)
- Does your company have the IT resources to operate duplicate/parallel IT systems? -
Most companies already do not have enough IT resources to correctly operate their
CURRENT IT environments.
-Most companies have already accrued substantial technical debt that has not been addressed.
-Is a new secure enclave a permissible and allowable IT burden?
-Have you defined the IT requirements and resources that will be required for a secure enclave?
-Has management signed off on the extra expense? - Does the company actually know where their existing CUI is located? (...or will it be located, if it is a new contract?)
- Who needs to be part of the secure enclave? Partners, vendors, subcontractors, some or all employees
- How will a secure enclave affect the company’s ability to collaborate and acquire and use business intelligence?
- Is it understood by management and IT that IT cannot be solely responsible for identifying CUI dataflow?
After answering the above questions, then it will be necessary to determine if you need a “Greenfield” or “Brownfield” enclave strategy.
10. Three CUI Enclave Use Cases
1st Use Case - A contractor is bidding on a RFP which contains CUI
Situation: The contractor wants to determine whether he/she can bid on an RFP, but the RFP itself contains CUI, therefore the contractor must be CMMCv2- level 2 certified in order to bid on the RFP. With this in mind, and assuming that it still makes sense to bid on a RFP that contains CUI, then the contractor must create, review and submit a proposal which will likely contain CUI in the following ways:
- CUI will be presented in various documents such as spreadsheets, word documents, diagrams and a PowerPoint.
- The contractor needs to be able to collaborate with a limited number of company employees using email, Teams and SharePoint to discuss the RFP and create the proposal, all of which contains CUI.
- In addition, the contractor needs to collaborate with one or more potential subcontractors, all of whom need to see the CUI-containing RFP.
Caveat 1: Since no contract has been awarded yet and there is no guarantee that anybody in this effort will be awarded a contract, all parties want to minimize their costs.
Caveat 2: It is assumed that from a business process standpoint, all work can be performed inside the proposed solution environment.
Solution Environment: The solution environment consists of the following:
- The contractor creates a CMMC compliant enclave inside the Microsoft Azure GCC (or possibly GCC-High) environment to work on this project
- Depending on the nature of the CUI, it is likely that Azure GCC is sufficient. If it is, that is dramatically less expensive to implement and easier to use.
- The contractor may choose to provide access to this enclave to potential subcontractors or may opt to make the sub(s) create a similar enclave of their own.
- The enclave includes virtual desktops inside the enclave and Microsoft Office 365 G3/G5 or E3/E5 licenses, depending on which environment is going to be implemented. Depending on the number of concurrent users needed, the number of virtual desktops needed is likely less than the number of office licenses. We use virtual desktops to make sure that no CUI data ever touches the user’s end computing device. The virtual desktop is configured to block any transfer of data from the GCC/GCC High environment to the end user’s computer.
- This enclave is hosted in the Azure government environment, so it is CERTIFIABLE, not certified.
- The contractor (and any subs) needs to complete all of the process items included in 800-171 like defining, documenting and implementing access controls, training, configuration management/change control processes, incident response, personnel security, physical security, etc.
- Then they need to configure the GCC/GCC High environment to meet CMMC requirements.
This solution minimizes the scope of the environment to be assessed for CMMC certification.
Costs:
- Microsoft licenses for GCC/GCC High including Office and virtual desktops
- Monthly recurring Azure hosting charges
- One-time costs to create and implement the business processes required to meet CMMC compliance requirements
- Recurring IT Operations costs (internal or external)
- Our one-time CMMC Compliance Program costs
- Optional but recommended TCPS pre-assessment to maximize the likelihood of passing the CMMC certification assessment.
- Cost of the actual certification by a C3PAO (we are not allowed to do the certification because we helped you get ready) and recertification every three years.
- Annual attestation letter from our vCISO?
- Annual attestation by YOUR CEO or Chairman of the Board (no direct cost but significant personal liability like fines and jail time).
NOTE 1: This exact solution/process has been used by some of the already approved C3PAOs who have been assessed and certified by the DIBCAC, so this will likely meet the test to be certified.
NOTE 2: If your company has ITAR requirements, this environment can be used to meet those requirements. That is one of the situations where GCC High is required.
2nd Use Case - Contractor wins the contract, but the use of CUI is relatively limited
Situation: The contractor has won the contract and may have one or a handful of subs as part of the contract. The contract calls out DFARS 252.204-7012 and likely, also -7019, -7020 and - 7021. It also requires the contractor to be CMMC version 2 level 2 certified. Finally, there is a mandatory flow down of these clauses to the subs who will need access to CUI data.
There are two sub-situations here.
The first is the sub-contractor(s) do not need access to any CUI data. In this case, the sub does not need to be CMMC certified, and this use case does not apply to that sub.
The second use case is that the sub-contractor(s) do need access to CUI data, in which case, this use case does apply.
Solution:
- In both cases, the contractor needs to do everything listed in use case one. A GCC or GCC High enclave, likely the one already set up for use case 1, will need to be provisioned, configured and maintained.
- Likely, ADDITIONAL LICENSES AND VIRTUAL DESKTOPS will be required as access to the CUI will increase
The important part here is that access to CUI is not pervasive to the company and to the business process. Required access is limited to a relatively small subset of employees and from a business process standpoint, maintaining and using the CUI data inside the enclave will work. The CUI will never leave the enclave.
Operationally, any employee, either contractor or sub, who needs access to the CUI data will connect to the virtual desktop in GCC/GCC High and access the data there. The GCC/GCC High environment will contain all the needed tools such as Office, Teams, Sharepoint and Email and any other tools will need to be provisioned for that environment.
Caveat: Some tools, because of their design, will not be compatible with the GCC/GCC High environment and alternatives will need to be identified and acquired.
Caveat 2: All process and GRC controls for 800-171/CMMC will need to be completed as required. This includes items like policies, procedures, training, physical security, etc.
Caveat 3: Any “sharing” of data, whether internally or externally, will need to be performed either inside this enclave or in another CMMC certified environment. All business processes need to be built around the fact that any CUI data must remain in the enclave or securely sent to another CMMC certified environment. For example, secure email is not available from employees’ phones or tablets
How is Use Case 2 different from Use Case 1?
- You have won the contract
- The number of people who need access is likely greater (REMEMBER DEPENDING ON THE CONTRACT REQUIREMENTS, ACCESS MAY REQUIRE US CITIZENSHIP FOR ALL PEOPLE ACCESSING THE ENVIRONMENT).
- The time period for operating the GCC/GCC High environment is no longer the length of the RFP response process (typically a month or a couple of months) but the length of the contract (typically years)
- The costs are now recoverable because they were baked into the RFP response. You eat all the costs for scenario 1 and those costs are never recovered.
- This is now a business-critical environment, so support requirements are greater. Less downtime can be tolerated
- Likely more applications will need to be integrated into the enclave
- Backups and DR/BC become more critical
3rd Use Case - Contractor wins the contract and CUI data is pervasive to the business process
Situation: The contractor has won the contract award and the contractor plus any subs are using CUI throughout their business processes. Process vendors are also using CUI.
Situation: The contractor’s IT environment and the IT environment of any subs and vendors that possess and use CUI must be fully CMMC compliant and both the contractor and the sub(s)/vendors must be CMMC version 2 level 2 certified. This includes any cloud services that may contain CUI as well as any cloud services that are part of the security infrastructure. Cloud providers may be able to use FedRAMP as an alternative to CMMC certification, but whether that will be allowed is still TBD. Depending on the level of CUI data, it is POSSIBLE that they may be able to self-certify versus being certified by an independent third party, but the details of whether that will be possible have not been released yet. Either way all parties that share CUI must be CMMC version 2 level 2 compliant.
Caveat: All parties will need to attest on an annual basis that they are compliant under threat of litigation under the False Claims Act. The government collects, on average, $5 billion a year in damages because of FCA litigation, so the threat is real. One of the reasons that the FCA is so effective is that a whistleblower gets to keep up to 30% of any fines that the government collects. This makes whistleblowing very attractive.
11. How to get paid for complying with 800-171 (Please see/share our video on this subject)
History: When the DoD first made assessment and certification a contract requirement, there was lots of squawking...mainly about how expensive it would be to do everything to get certified. The DoD then replied. “You have been attesting all this time that you are in compliance with 800-171. The only NEW expense should be the cost of the certification assessment. All other expenses should be built into the overhead of your existing contract(s). This has already been authorized by DoD. So... since you say you are complying already, then quit squawking about how expensive this whole compliance thing is going to be.” Any ongoing, recurring costs are allowable and should be calculated when pricing your response. For example, if you are paying for an ongoing Security Operations Center as a Service (or even internal), those costs recur every month or year, so those costs can be included as allowable.
You should also get these calculations squared away for all NEW contracts
The following costs should be calculated BEFORE submitting any new contract proposals:
- Either IT infrastructure upgrade or enclave implementation
- Changes to business processes to support this
- Employee training
- On-going support and maintenance
- Other costs involved in protecting CUI
- How remote workers will be supported
- How traveling workers will be supported
12. Cost and Other Issues Related to the Necessary Use of the Microsoft Government Cloud for enclaves
CUI data and infrastructure must be located within an approved government cloud environment. This requires a license to use the Azure government cloud and licenses for software, like Microsoft Office and other software that will be used inside the enclave. Use the following table to determine which subscription is best for you.
Microsoft Government Cloud Pricing Matrix (there doesn’t seem to be any prices here)
https://www.nimbus-logic.com/gcc-high-pricing-and-licensing/Please answer the following:
- Do your business requirements dictate that certain applications must operate in the new cloud/enclave environment? If yes, we need to determine if these applications are supported in this environment.
- Do you need to bring in any existing CUI data into this environment…or is all the data new and part of a new contract?
- Do you need to integrate an existing Active Directory into the new environment or set up a new AD? If possible, we suggest a new AD.
13. Calculating Enclave Costs
- Monthly Microsoft government cloud infrastructure subscription
- Monthly cloud infrastructure usage charges
- Third-party software licenses, if any
- Any additional infrastructure architecture/migration services
- Ongoing IT support costs, either internal or external
- Other 800-171 compliance costs (our CUI Program costs)
If everything is new…we call this a “Greenfield” enclave. And there are no data migration charges. A Greenfield enclave is faster to set up and less expensive.
14.What are MSP/MSSP requirements associated with an enclave environment?
Questions to ask your MSP or MSSP
- Need strong trust and working relationships
- Do you have any DoD DIB customers who have already implemented CMMC programs? If not, there is so much underlying knowledge they don’t have, that just will not work out.
- If they are not willing to take any DFARs flow downs into their contract so you have shared accountability, then this is a problem. They must sit at the audit table with you. If they cannot or will not accept the flow downs, then you will have to find a different MSP. You will be in breach of contract if the flow downs are not in your contract with your MSP.
15. Why choose us as your CMMC/800-171 partner? --Our CMMC Level 2 Enclave Certification Program
What do we do about protecting ourselves with respect to DoD contractor clients …and presenting ourselves as the right partner.
Why choose us as your CMMC/800-171 partner?
- Update our MSA to include language about our compliance
- Update our MSA to include language about CUI, flowdown, MSP, etc.
- Document our own architectures and controls
- Document our experience with CMMC requirements, etc
Architecture Services
Need architecture to facilitate collaboration between between the enclave and the mothership How to do this and minimize increase in risk
Our services include:
- Helping you determine answers to the above
- Helping you analyze and determine business, IT, and enclave environment requirements
- Support the training of your IT team to manage an enclave
- Supporting/managing any migration or implementation processes (including environment configurations)
- Supporting the life of project
- Ensuring 800-171/CMMC compliance
-Policies & procedures (monitoring, training, assessments, vendor management, etc.)
-On-going coaching - Evaluate/manage MSP
- Support you during CMMC audits
- Helping you identify and vette any additional third-party technical tools required for CMMC certification
Cost-effective tools and services designed for CMMC compliance
Annual Risk Assessment based on framework
- Strategic/operational questions plus follow-up as per compliance requirements
- Lightweight EASM report
- External network vulnerability scan where we look at all devices and vulnerabilities
- Internal vulnerability scan one time
- External penetration test-one time event
- Internal penetration test-one time event ASM only (looks at public info)
- Internal vulnerability scan subscription (BelArc)
Trava Security-new…this is IASM plus EASM–does better job of continuous monitoring requirement than EASMternal New thing-subscription
- Internal and external VS
- RA management tool (RA separate)
- Medium EASM
- Un-Authenticated and authenticated
- This tool does not look at vendors like KB and BS does
- Talking to insurance companies about bundling this product into insurance program
- $200/mo/client our price or $2000/mo for as many as you want
- VS scan and logging and alerting. Two different requirements.
- Customer visible
Why we are credible and worth listening to on this subject
The authors of this white paper know what they are talking about. The reasons for this statement are as follows:
- The authors have been active RPO and RP members of the CMMC Accreditation Body (AB) since its inception and regularly engage with CMMC AB leadership.
- In January of 2021 and in conjunction with one of the original founding board members of the CMMC Accreditation Body (AB), the authors of this white paper publicly questioned DoD CMMC compliance strategy and encouraged consideration of enclave strategies. This activity led to multiple conversations within DoD procurement channels which (in our opinion) likely influenced the current conversation around enclaves.
- Raymond Hutchins and Mitch Tanenbaum operate two cybersecurity companies (CyberCecurity and Turnkey Cybersecurity and Privacy Solutions) that have been providing DoD-related cybersecurity services since 2015. Mitch is a nationally recognized 800-171/CMMC 2.0 compliance expert. Mitch’s history with the DoD started when he was put in charge of Texas Instruments Defense Systems information security program. He writes and speaks about DoD compliance and cybersecurity issues regularly. Please see his blog HERE.
