Protecting Your AzureAD Admin Portal
Note: This tip came from a blog post created by Per Larsen, a Microsoft MVP in Atea, Denmark, who works with Microsoft products such as EM+S, Intune, System Center and Azure. The original post can be found at https://osddeployment.dk/2017/06/24/a-standard-azuread-user-have-access-to-browse-the-admin-portal/ . I have made some grammar and editorial changes to the original post.
For some strange reason, by default, Microsoft makes part of the admin portal of Active Directory in Azure visible to the average authenticated user. While they cannot make changes, what is visible is way too sensitive. The solution to this is to deploy Microsoft’s conditional access tool, described below. Conditional access is an optional part of Office 365 called Enterprise Mobility and Security or EM+S. It is only available to Enterprise licensed Office customers. Information on EM+S can be found at https://www.microsoft.com/en-us/cloud-platform/enterprise-mobility-security-pricing .
In an on-premise Active Directory installation, a normal user can read the directory by default using a LDAP browser. We put a firewall and other security measures in place outsiders cannot access the directory.
When we use Azure Active Directory – there are often no security measures in place. In some installations, ADFS is the only security measure – ADFS is used to login in to Azure AD without having the user’s password in the cloud – but the ADFS is setup to allow all authenticated users to see the directory.
What is the problem:
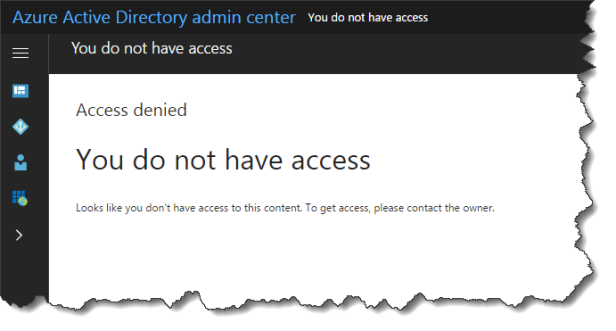
When a user logs in to the old Azure AD portal https://manage.windowsazure.com the user gets this message:
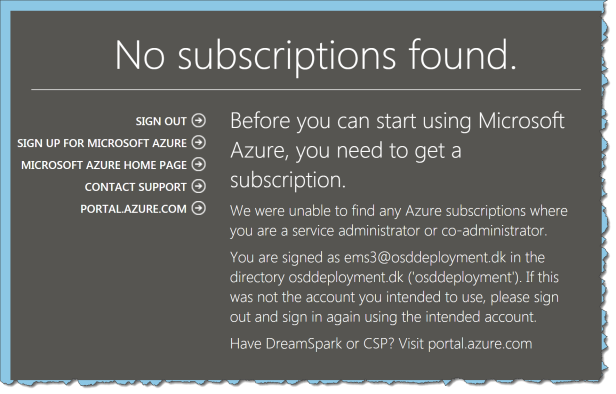
No access – no problem!
When the user log in to the new Azure AD portal https://aad.portal.azure.com the use gets this:
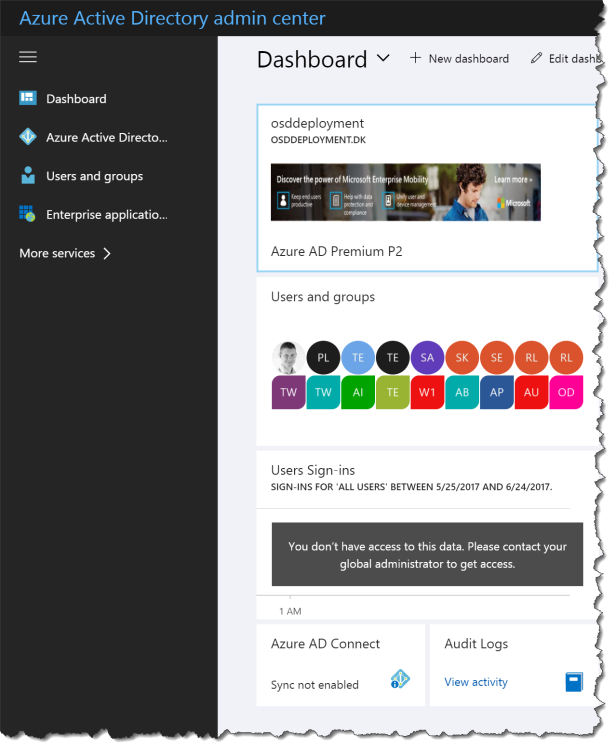
The user cannot see all setting and cannot change anything, but still this is a security issue.
What is the solutions:
The quick fix for this is Conditional Access on the cloud App Microsoft Azure Management.
How to setup Conditional Access for Microsoft Azure Management:
Login with a admin to https://aad.portal.azure.com
Go to Security – Conditional access
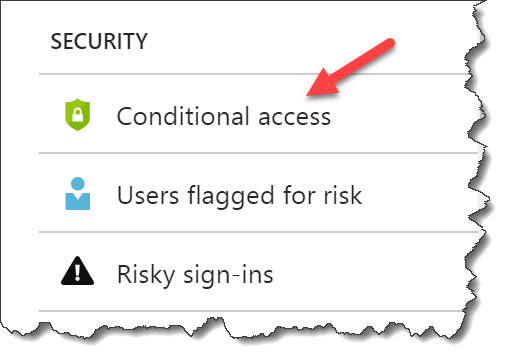
Click New policy
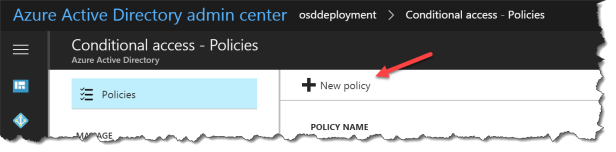
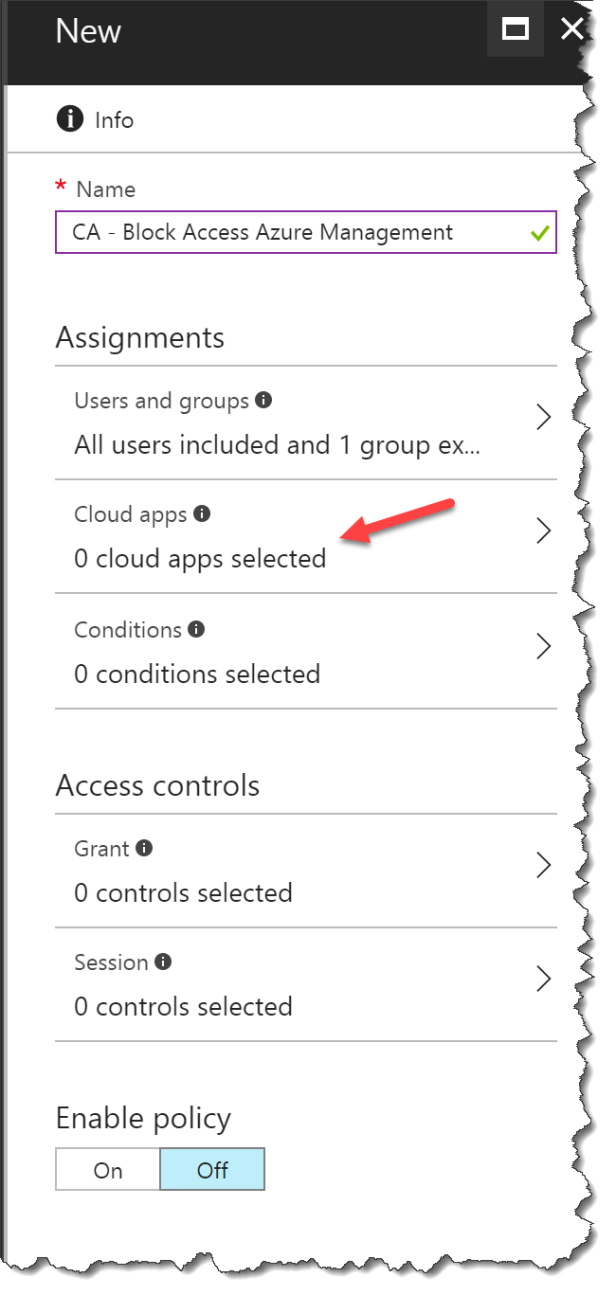
Give the CA policy a name
Click on Users and groups
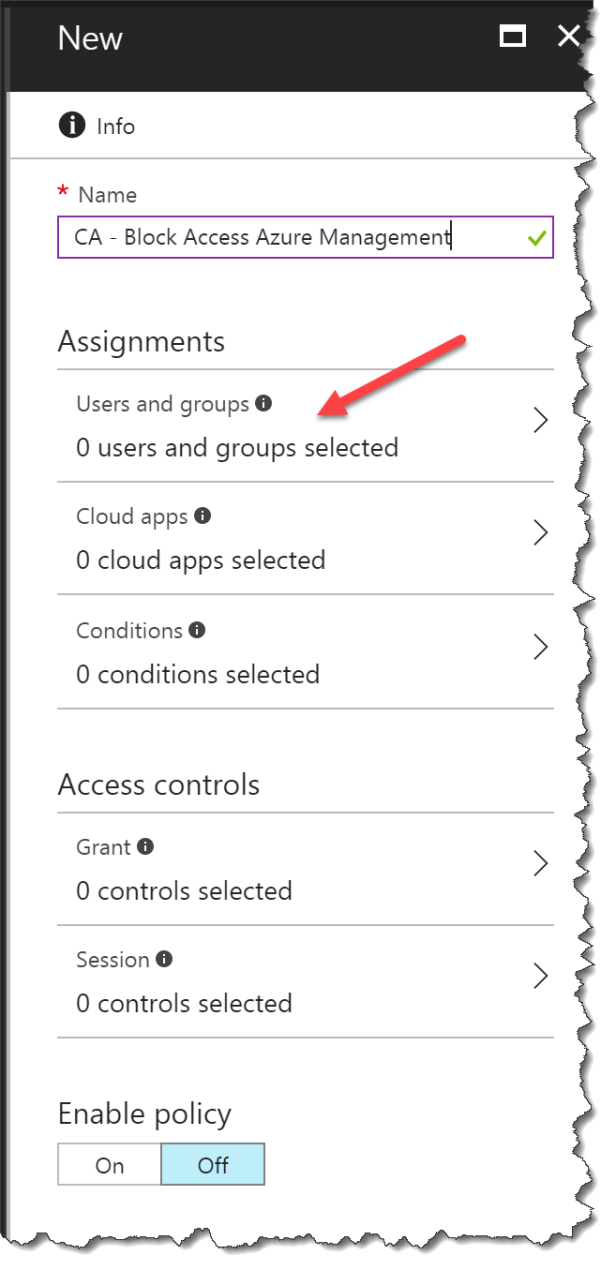
Select All users
Remember to select an Exclude user or you lock yourself out from changing this policy
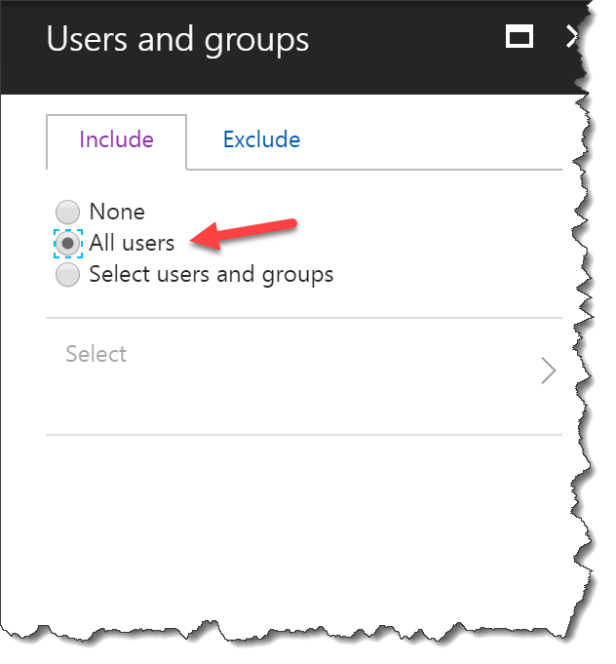
Select Exclude
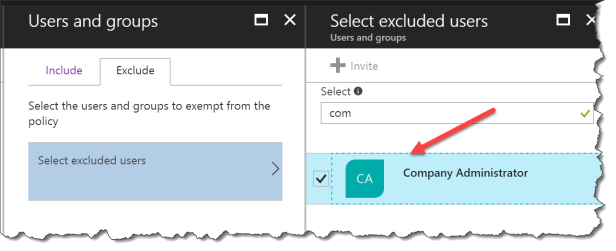
Click Select excluded users
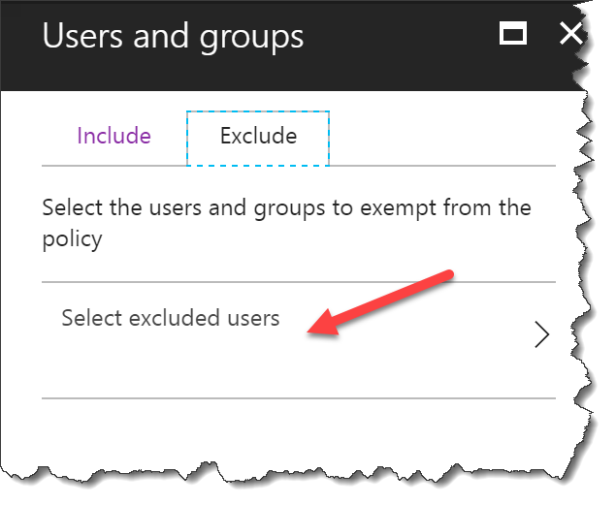
Select a group with least one global admin !!!
Select Cloud apps
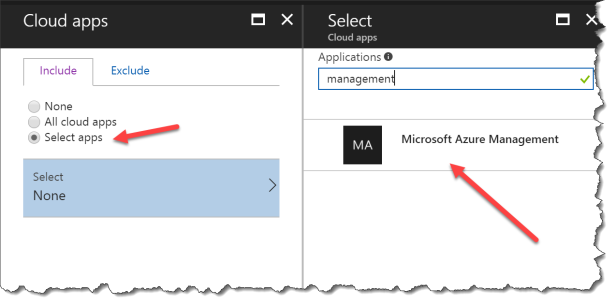
Click Select apps
Search for Microsoft Azure Management and select the app
Select Conditions
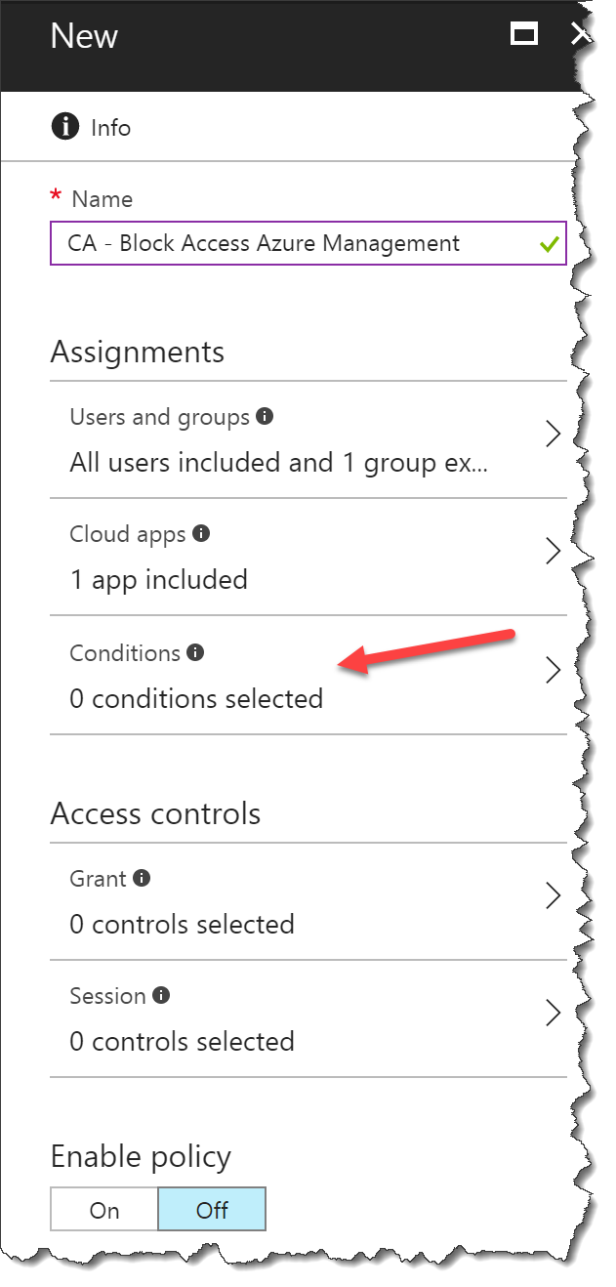
Select Client apps
Click Yes – the both Browser and Mobile apps and desktop clients will be blocked
Info: Use Locations if you only whats this to apply outside your trusted network
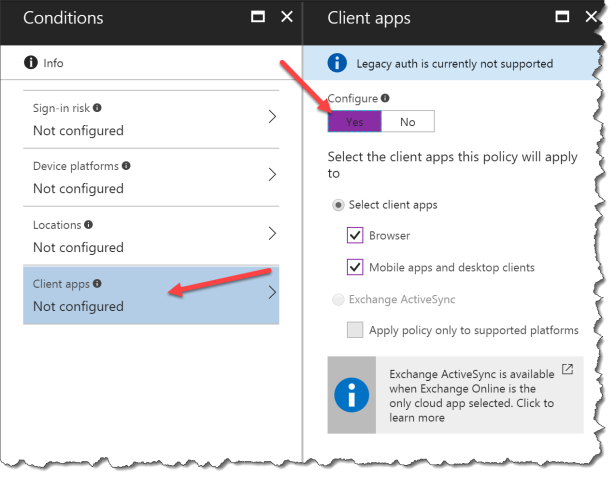
Select Grant
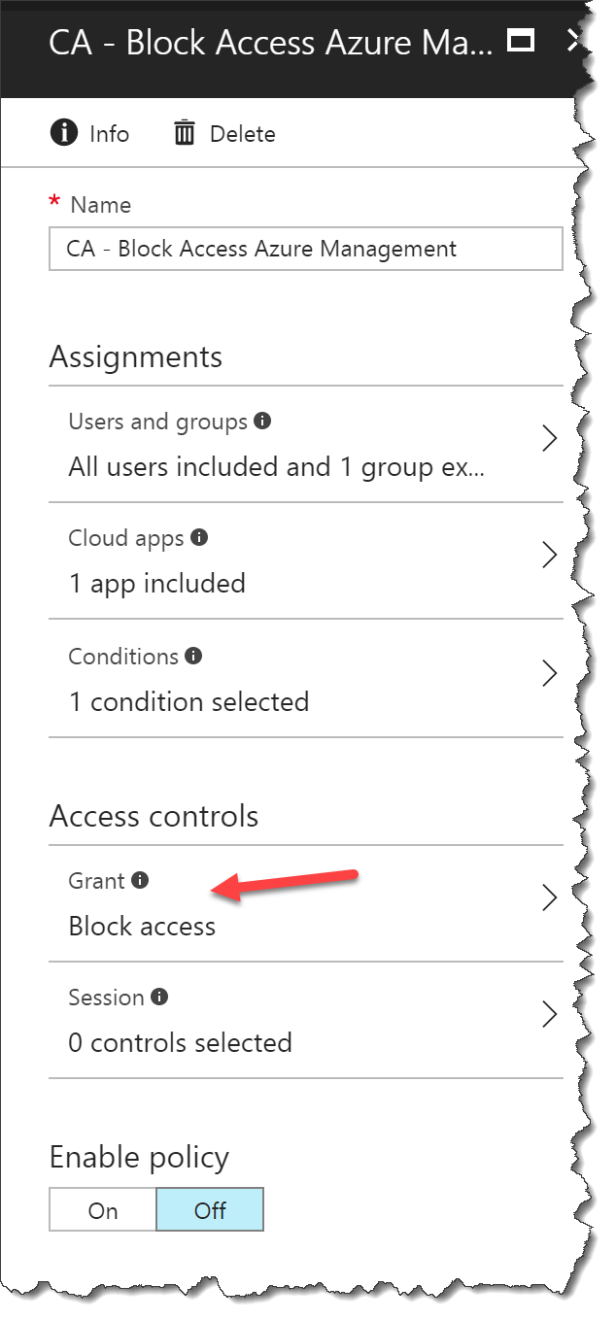
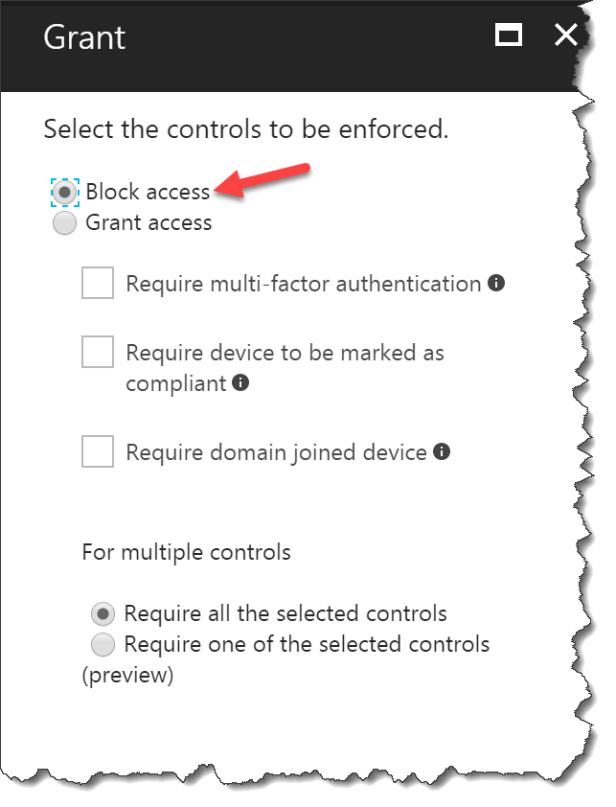
Click Block access
Click On to enable the Conditional Access policy
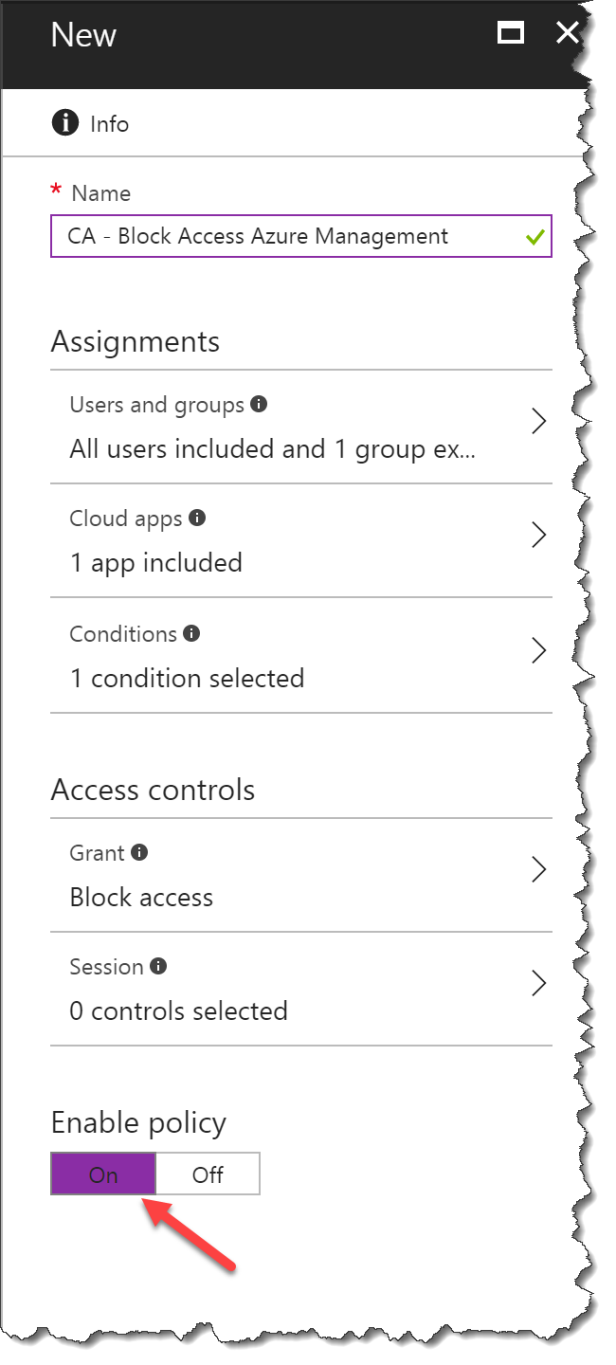
Now you have blocked the access for standard users from accessing your AzureAD.
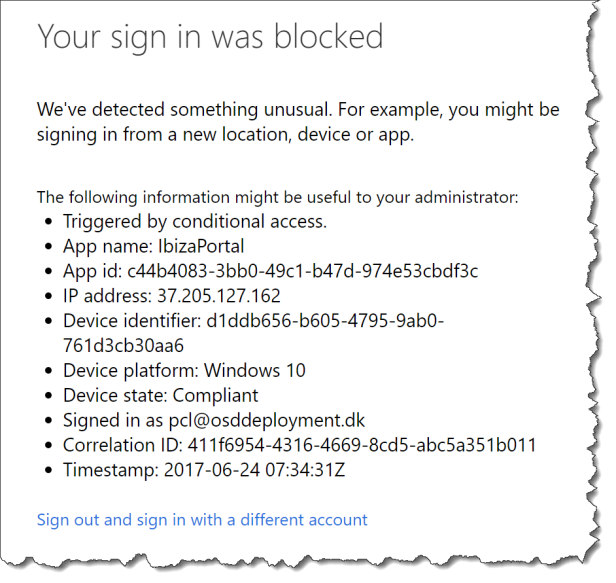
When the policies is in effect the user will get this message when accessing the Azure portal from a browser or from the mobile Azure app
There is also another way to do this:
Conditional Access requires Azure AD Premium license – if you don’t have that there is also another way.
This will only apply to standard users – and not a user with privileged access (User administrator, password administrator, etc.) and you cannot do inside/outside rule like in the Conditional Access.
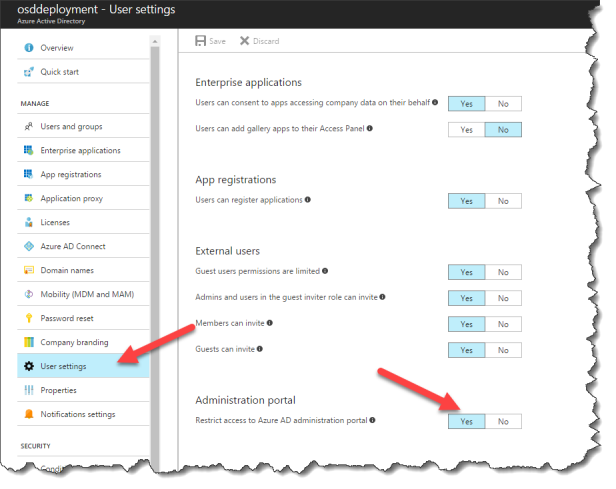
Inside the Azure AD you can set:
Go to User settings – Administration portal
Restrict Access to Azure AD administration portal to Yes.
This will not block your users from accessing https://portal.azure.com
This will only create a Access denied when accessing the AzureAD