The DoD has been working to improve cybersecurity over the last several years as news of nation- state sponsored theft of defense secrets makes the news on a regular basis. The biggest source of leaks of sensitive intellectual property is the hundreds of thousands of contractors that have access to sensitive but unclassified information called CONTROLLED UNCLASSIFIED INFORMATION or CUI.
In 2013 the DoD created a security requirement in the Defense Federal Acquisition Regulations called DFARS 252.204-7012 and then a few years later, NIST released a security requirement named SP 800-171. While both of these were a start to improving security for the defense industrial base, they didn't solve the problem.
December 2023 CMMC Update
Just before Christmas 2023 the Defense Department released the most recent draft version of the CMMC regulation. Next comes a 60-day comment period and all of what follows in the normal federal government regulatory process. This means that this regulation will not become mandatory, most likely, until very late 2024 or early 2025. At that point, the regulation may appear in new contracts, but it won’t appear in all contracts, at least for several years.
This newest version is only part of the overall cybersecurity regulation; there is another part still to come, so we are not done with the regulatory process.
In addition, the GSA has released a separate proposed update to the general government cybersecurity requirements currently found under FAR 52.204-21. That will update the security requirements for contractors that do business with the federal government but do not have access to CUI. More to come on that.
Controlled Unclassified Information or CUI was created after 9/11 via a presidential memorandum signed by President Bush. It was updated in 2011 by President Obama under Executive Order 13556. The Pentagon and other parts of the government are still working on implementing this 20 years later.
CUI is government created or owned information that requires safeguarding or dissemination controls consistent with applicable laws, regulations and government wide policies.
CUI is not classified information. It is not corporate intellectual property unless created for or included in requirements related to a government contract. It is information that we do not want to fall into our adversary’s hands. An example of this is the design of the F-35 fighter, which China stole and then built their own. Contractors can create CUI, but only as part of a contract. The contract’s CRDLs should state whether a particular deliverable should be marked as CUI and the specifics of the required markings (distributions A thru F). Anything other than Distribution A is likely CUI, but might not be CUI.
Because there are fewer controls over CUI as compared to classified information, CUI is the path of least resistance for adversaries. Loss of aggregated CUI is the one of the most significant risks to national security, directly affecting lethality of our warfighters.
The problem was that people were claiming that they were compliant with these regulations, specifically NIST SP 800-171, but they were not compliant, and no one was checking to verify it.
In early 2019 DoD upped the ante by releasing the Cybersecurity Maturity Model Certification (CMMC). This was the first time DoD required contractors, subcontractors and suppliers to be CERTIFIED to participate in the DoD supply chain.

The DoD released version 1 of CMMC as an emergency requirement and while that allowed them to deploy it quickly, it didn’t mean that it was going to be painless. In fact, especially for small businesses, CMMC 1.0 was quite painful and expensive to implement. As part of the emergency rule-making process, DoD was required to conduct a review and make changes if needed. That review was supposed to be complete in April of 2021. It was released in November 2021.
In November DoD released CMMC 2.0. Here is what was in that change.This is now updated again with the DoD’s 2023 Christmas present to contractors (the most recent version of the rule)
1. The five levels of CMMC are now three. Since the DoD never planned to certify anyone at levels 2 or 4, this is no loss and doesn’t really change much.
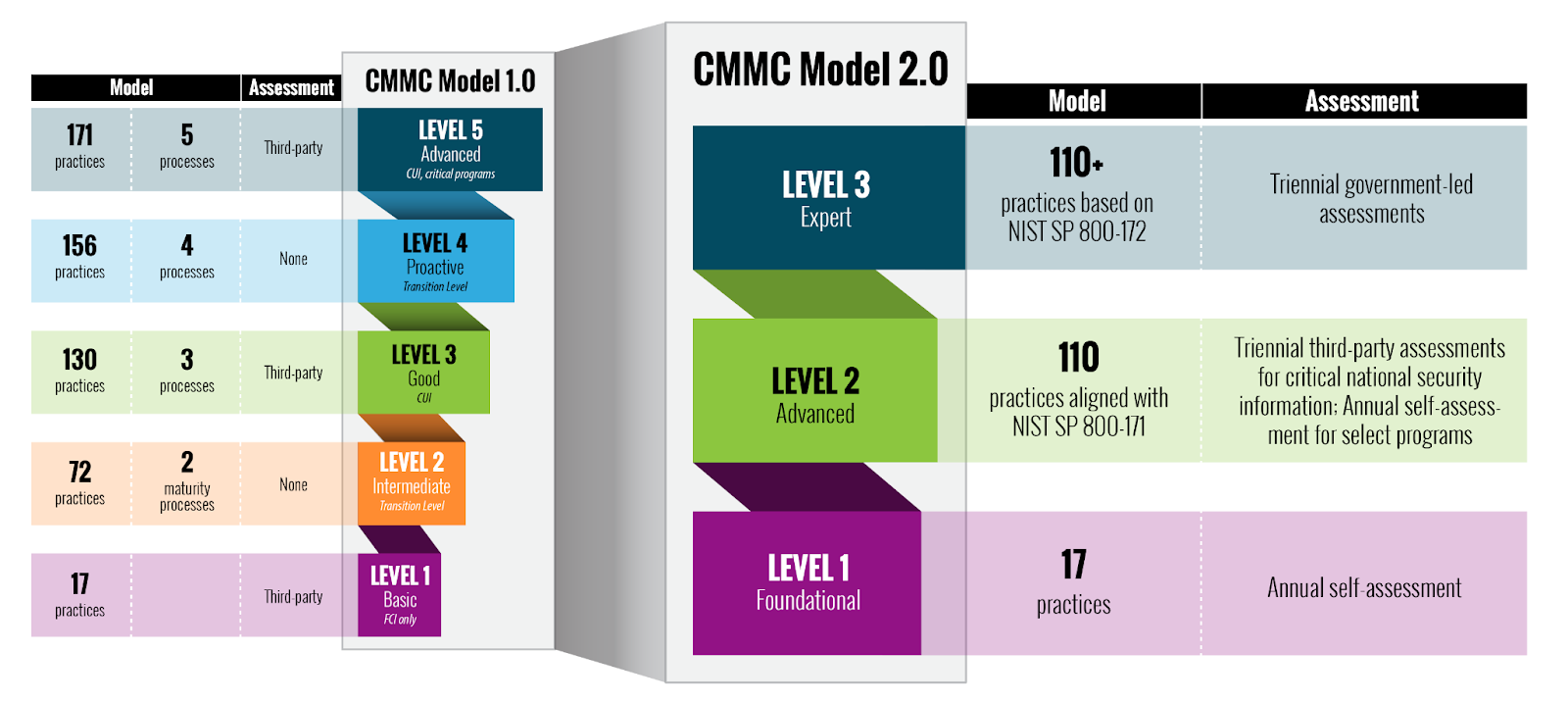
2. Contractors that have to comply with Level 1 can self-certify. These companies only need to have very basic security so self-certifying is a pretty low risk. Note that you cannot have access to CUI at level 1.
3. CMMC 1.0 Level 3, now called Level 2, may be split into two sublevels with the lower sublevel able to self-certify. The DoD has not explained how they are going to decide who can have access to CUI and self-certify and who has to have a third-party certify them. For those lucky ones who can self-certify, they have just reduced their compliance cost by tens of thousands of dollars. The higher level 2 companies will still need to get a third-party certification, just like the old level 3. It is anticipated that only 10-15% of folks at Level 2 will be able to self-certify. In the most recent version of the proposed rule a few contractors, maybe ten percent, will be able to self certify at level 2, but they still have not explained how that is going to work.
4. Level 3 is going to require both a Level 2 third-party certification and also an extra certification done by DoD. They have not figured out how Level 3 is going to work, but that should not affect most contractors. It will probably be mostly those working for the intelligence community.
5. The 20 extra controls that were in CMMC 1.0 are gone, but only for now. The DoD has said that they are going to ask NIST to add them to the next version of 800-171, so this is only a short-lived reprieve.
6. The Process Maturity Levels from CMMC 1.0 are gone. These are probably gone forever, but you really should be doing these anyway. You just won’t be tested on them.
7. The Department of Justice says publicly that they are going to file lawsuits against companies that have lied about their 800-171 compliance. We have seen two settlements thus far, but expect more. This is a big stick because if the DoJ wins, a company could be disqualified from receiving any DoD contracts and can be fined millions of dollars.
8. The CMMC-AB (now referred to as the Cyber AB), in our opinion, is going to be in a holding pattern for the next year or two. With no published regulation, it is going to be hard to move forward. They are encouraging folks to voluntarily get certified. We assume most won't do this, but for those who do, there could be more government business.
9. The DoD says that they want to create some sort of incentive for companies to get certified before the regulation is finalized. They have not said how that is going to work. Or, even if they have the authority to do that.
10. Certifications will expire. For self-certifications, an executive of the company will need to sign that they understand what they are signing and that everything that they have attested to (as in that they are fully compliant with 800-171) is true. You will have to do this every year. This is an easy place for the DoJ to come after you for fraud, disqualify you for future contracts or place onerous requirements on you.
At the higher levels, certifications will last three years.
It is also possible (or even likely) that the Pentagon may require that classified network owners be certified as well, although they have not said this publicly. Yet.
Note that while companies at level 2 and above only need a third-party certification every three years, the CEO or equivalent needs to sign an attestation every year that states that (a) they understand what they are signing and (b) that they are fully compliant with all of the requirements. That means, in principal, that companies need to do a self-certification every year. If they don’t do that the CEO will not be able to know if what are signing is true, running the risk of false claims act penalties and even getting barred from government contracts.
The CMMC will encompass three maturity levels that range from "Foundational" to "Expert". The intent is to identify the required CMMC level in RFP sections L and M and use it as a "go / no go decision."
As promised, NIST is working on a new version of 800-171. Called Revision 3 or Rev 3, it makes significant changes to the current version. The way the regulation (DFARS 204-252-7012) reads, a contractor --- and all of their subs --- is required to comply with THE THEN CURRENT VERSION of SP 800-171 when the contract is signed. We anticipate that Rev 3 will be released in its final form in early 2024. That means that contracts signed after Q1 2024 will likely need to comply with 800-171 Rev 3 unless the Defense Department chooses to provide a limited or blanket waiver of that requirement for a few months.
There are three entirely new sections in 800-171 Rev 3, mostly affecting supply chain security and contractor’s acquisition processes. It also brings back the requirement for written policies and procedures which were sort of removed between CMMC 1.0 and 2.0, but not really. The requirement for having those policies and procedures never really left; they were buried in appendix E of 800-171. What NIST discovered was that people were ignoring the requirements in Appendix E (there were more than 50 that applied to contractors), so they moved all but 17 into the main standard document.
The current status of Rev 3 is that NIST has released the final public draft has been released, along with the initial public draft of 800-171a, which is the guide for assessors. We expect that the final approved version will be released in Q1 2024. At that point, it is up to the Pentagon to decide how quickly contractors will be required to comply with Rev 3. It is possible that they will make contract mods to require existing contracts to comply with Rev 3, but, certainly, new contracts will be required to comply after a phase-in period. If they do push contact mods, it is important that contactors know what they are signing and potentially ask for more money for these new requirements.
Third-party analysis shows that there are 50 percent more assessment requirements in revision 3 than in the current revision.
While there has been a lot of focus on the -7012 DFARS clause, there is a family of clauses which are all inter- related. Here is the family DFARS clauses relevant to CMMC:
The Defense Federal Acquisition Regulation Supplement (DFARS) represents the standard contract clauses that the Defense Department uses for ensuring that vendors agree to DOD’s contract requirements. When it comes to security, there are several DFARS clauses that directly apply:
252.204-7008 – COMPLIANCE WITH SAFEGUARDING COVERED DEFENSE INFORMATION CONTROLS. This clause states that the contractor agrees that it will implement all security controls required by NIST SP 800-171 no later than December 31, 2017.
252.204-7012 - SAFEGUARDING COVERED DEFENSE INFORMATION AND CYBER INCIDENT REPORTING. This DFARS clause effectively reiterates what is in the clause above and adds to it the requirement to report any cyber incident to the DoD within 72 hours.
252.204-7019 - NOTICE OF NIST SP 800-171 DOD ASSESSMENT REQUIREMENTS. This DFARS clause requires contractors to conduct a low-confidence self assessment of their 800- 171 compliance and post the results to a DoD run system called the Supplier Performance Risk System (SPRS). It also gives the DoD the right to conduct its own medium assurance or high assurance assessment, either virtually or on site, if deemed appropriate.
252.204-7020 - NIST SP 800-171 DOD ASSESSMENT REQUIREMENTS. This clause says that DoD will not award a contract to a contractor who has not completed at least a basic (low confidence) 800-171 self assessment in the last three years and posted the results of that to SPRS. This also says that a contractor shall provide access to its facilities for the DoD to conduct its own assessment if appropriate.
252.204-7021 - CMMC REQUIREMENTS. This clause says that the contractor shall have a CMMC certification no more than three years old, that this clause must be inserted into all subcontracts and that all subcontractors must have a CMMC certification at the appropriate level for the information being shared.
252.204-7024 - NOTICE ON THE USE OF THE SUPPLIER PERFORMANCE RISK SYSTEM (SPRS). This clause says that contracting officer must use the data in SPRS in managing the risk of awarding the contract to any vendor. One of the items in SPRS is the vendor’s 800-171 compliance score.
To be clear, the DoD does not control what is in 800-171. That is the responsibility of the Department of Commerce. Likewise, the Department of Commerce doesn’t control CMMC. If you don’t like what is in 800-171, talk to Commerce; DoD can’t change it. If you don’t like CMMC, talk to the Department of Defense.
CMMC is a program to make sure that contractors who say they are complying with 800-171 really are complying. CMMC is a third-party, independent assessment of a contractor’s compliance status with the NIST standard. That is ALL CMMC is. CMMC does not have any of its own requirements any longer.
The DoD has built upon existing DFARS 252.204-7012 regulation and developed the CMMC program as a “verification component” with respect to cybersecurity requirements. The DoD has entrusted DoD contractors to achieve compliance and (with continued pressure) to ensure 100% adoption of cybersecurity controls—as the DoD is updating its policies. This is a “trust but verify” process.
The DoD is putting a lot of pressure on the big primes to get their subs in line. Of course, the primes don’t have their own houses in order yet. The prime contractors are required to flow down the appropriate CMMC requirement to subcontractors and the subs must flow down these requirements to their subs. DoD considers subcontracting may flow down to ten levels of subcontracting.
If you have a vendor that has access to your systems such as an IT services provider or you have a vendor that you give either system access or data, any of those third parties will likely need to be certified at the same level as you are or above. The current DFARS -7012 and -7019 are MANDATORY flow down clauses with no changes other than you can insert your company’s name. Since almost all companies use vendors or service providers, this is going to be a big one. When CMMC is fully rolled out, any subs or vendors used on the contract will need to be certified at the appropriate level before the contract can be awarded.
The DoD still plans on maintaining a database that contracting officers will review prior to awarding contracts. What this looks like is still undefined. It will probably look something like SPRS plus other systems. The database will also include the CEO’s self-certification information to keep the pressure on those CEOs.
A lot of the focus has been on CMMC (Cybersecurity Maturity Model Certification) Level 2 which includes all contractors who have access to or create Controlled Unclassified Information or CUI (pronounced koo-ee). CUI includes a wide variety of information from plans and schematics of systems and facilities to mundane things like how many pairs of what kind of boots are being sent to which base. While CMMC Level 2 affects a percentage of the DIB, CMMC Level 1 affects every company that signs a contract with the Defense Department or subcontracts to someone who does.
You might ask well what is the difference between CMMC Level 1 and Level 2. That is a very important question.
For companies that need to comply with CMMC Level 2, they have to satisfy 110 controls and over 300 assessment objectives. These assessment objectives are defined in the NIST SP 800-171A standard that is the core of CMMC.
For those companies that do not have access to any CUI, they still need to comply with CMMC Level 1. That means that they have to satisfy 17 controls and over 60 assessment objectives.
For CMMC Level 2, you probably will have hire a third party to “validate” that you are meeting all of the 300 plus assessment objectives. (a small percentage of contractors will be able to self-assess) For CMMC Level 1, it is more of an honor system. The CEO, President or similar title must sign off each year that you are in compliance with those 60 plus controls. Similar to Sarbanes-Oxley for public companies, the Justice Department can sue you under the False Claims Act if you lie. In addition, if a disgruntled employee or ex-employee rats you out, they will get about 30 percent of whatever fine the government assesses. Recently, the government fined a company about $250 million and the snitch received a check for more than $70 million – which is a strong incentive if someone is unhappy with you. In the worst-case scenario, you can be barred from government contracts for several years.
While these two Levels are the only two that are currently defined for CMMC (there will be a Level 3 later that will apply to a smaller group of contractors who mostly deal with intelligence information), there is a “middle of the road" objective that some companies are being asked about. That is NIST SP 800-171 Basic Controls. There are 31 Basic controls and over 100 assessment objectives to be compliant with this. While there is no CMMC standard for this, some companies are being asked about it.
For companies just starting out on their CMMC journey, start with the Level 1 controls, since everyone will have to meet these. Then, if you have a requirement to be Level 2 certified, complete the Basic controls. That will get you about one-third of the way through the process and will represent another milestone. Finally, complete the rest of the 110 controls.
While this program has taken longer to roll out than initially anticipated, it is a huge change that ramifications throughout the entire defense industrial base, so this is not really a surprise.
Ultimately, DoD contractors will not be awarded contracts unless they are certified at the required level. This is different than what has been the norm historically. Historically, contractors get certified after the fact. The plan has changed. Now you will have to be certified in advance.
DoD Contractors will need either to self-certify or coordinate directly with an accredited, independent, commercial certification organization to request and schedule a CMMC assessment. If they need to get to CMMC 2.0 Level 3, they will also need to coordinate with the DoD after they have their third-party certification. Currently, there are less than 50 approved certifiers, but there are hundreds in the pipeline. That means that in the short term there will be a wait, once you are ready, to actually be assessed, but that will likely change by late 2024-early 2025. NOTE THAT ASSESSORS WILL NOT EVEN SCHEDULE YOU FOR AN ASSESSMENT IF THEY DON’T THINK YOU ARE READY – see the next section on getting prepared.
DoD contractors or suppliers who have the skill, resources and IT staff available, can meet the appropriate CMMC level of cybersecurity in-house. You can follow the same guide that the assessors will, NIST SP 800-171A, but let us warn you, the devil is in the details and the devil may cause you to fail the certification process. If you fail, you get to fix the problems and then pay again for another certification try.
For many DoD contractors, the most effective way to meet the CMMC cybersecurity requirements is to outsource the task to a consulting partner that has the appropriate expertise and can work with you to become compliant. Remember that DoD contractors remain ultimately responsible for ensuring that their company meets the appropriate cybersecurity requirements, so it is essential to choose a provider that is reputable. Again, you will have to engage a third party for the actual certification process. It is our experience that very few organizations will be able to get prepared without engaging a consultant. Certainly, do what you can by yourself, but your view of what prepared means is likely viewed through a biased lens. The third party, who answers to the Pentagon (DoD will review 100% of all early assessments), is going to be much stricter in their interpretation of the requirements.
CyberCecurity, LLC and Turnkey Cybersecurity and Privacy Solutions, LLC are two such cybersecurity consulting companies.
The first step towards compliance is to determine what CUI information you have, how it is used and who needs access to it. Then you should conduct a gap assessment to determine how close the contractor is to compliance. This process is called a risk assessment or gap analysis. Gap analyses are designed to discover areas where the company is not fully compliant with the regulations.
The results of the gap analysis may reveal issues related to:
Without a gap analysis, it's impossible to know what changes an organization needs to make before it meets the required CMMC Level. The gap analysis provides a roadmap to becoming compliant.
Certification is a point-in-time event. Even if it covers some historical period like an AICPA SOC Type 1 audit does, it doesn't mean that you will be compliant in the future.
The DFARS also require almost instant notification (within 72 hours) of a security event to your prime contractor or to the government. Part of being compliant is being able to respond to these incidents in a time frame and with the required data to the appropriate party. There are additional, significant requirements to comply with in case of a breach.
For many companies, DoD contracts make up a substantial percentage of their revenue and because NIST SP 800-171 is a requirement in many cases for bidding on contracts (check with your contracting officer), it's extremely important that contractors are complying with 800-171. If a contractor lies about being 800-171 compliant, they can be fined and debarred.
CyberCecurity, LLC and Turnkey Cybersecurity and Privacy Solutions, LLC are full-service cybersecurity companies that offer a wide range of cybersecurity and privacy services, including various certification services. More information about our certification services, please give us a call (info below).
We currently offer:
Accomplishing the above items will facilitate becoming compliant with the CURRENT, EXISTING, ONGOING DFARS.
Have more questions?
Please call me for more information: Mitch Tanenbaum, CISO, CyberCecurity, LLC